Nessus | TryHackMe Walkthrough
Lab Access: https://tryhackme.com/room/rpnessusredux

Nessus vulnerability scanner is exactly what you think is its! A vulnerability scanner! It uses techniques similar to Nmap to find and report vulnerabilities, which are then, presented in a nice GUI for us to look at. Nessus is different from other scanners as it doesn’t make assumptions when scanning, like assuming the web application is running on port 80 for instance.
Nessus offers a free and paid service, in which some features are left out from the free to make you more inclined to buy the paid service. Their pricing is similar to Burp Suite, so unless you got some spare change, we will be just be using their free version.
You can check out their pricing options here: https://www.tenable.com/products/nessus

[Question 1.1] — I have read the description!
Answer: No answer needed.

[Question 2.1 to 2.10]
It does not require any answer at all, but all that is required is to follow the exact instructions provided by THM, which I have tested and it flows perfectly, and they have made it extremely easy to implement Nessus into your machine.
Answer: No answer needed.

This section is rather straightforward because all that is required is to read the description for each tool and understand its function, and it would be beneficial to learn more about what it actually performs.
[Question 3.1] What is the name of the button which is used to launch a scan?
Answer: New Scan
[Question 3.2] — What side menu option allows us to create custom templates?
Answer: Policies
[Question 3.3] What menu allows us to change plugin properties such as hiding them or changing their severity?
Answer: Plugin Rules
[Question 3.4] In the ‘Scan Templates’ section after clicking on ‘New Scan’, what scan allows us to see simply what hosts are alive?
Answer: Host Discovery
[Question 3.5] One of the most useful scan types, which is considered to be ‘suitable for any host’?
Answer: Basic Network Scan
[Question 3.6] What scan allows you to ‘Authenticate to hosts and enumerate missing updates’?
Answer: Credentialed Patch Audit
[Question 3.7] What scan is specifically used for scanning Web Applications?
Answer: Web Application Tests

[Question 4.1] Create a new ‘Basic Network Scan’ targeting the deployed VM. What option can we set under ‘BASIC’ (on the left) to set a time for this scan to run? This can be very useful when network congestion is an issue.
Answer: Schedule
[Question 4.2] Under ‘DISCOVERY’ (on the left) set the ‘Scan Type’ to cover ports 1–65535. What is this type called?
Answer: Port scan (all ports)
[Question 4.3] What ‘Scan Type’ can we change to under ‘ADVANCED’ for lower bandwidth connection?
Answer: Scan low bandwidth links
[Question 4.4] With these options set, launch the scan.
Followed exactly the answers given above EXCEPT for the “schedule” component, or else the scan would wait till the schedule time was up before commencing.
1st - In Scanner > Select "Basic Network Scan"
2nd - Discovery > Scan Type > Select "Port scan (all ports)"
3rd - Advanced > Scan Type > Select "Scan low bandwidth links"If no results display, make sure you're connected to the OpenVPN provided by THM, or it simply doesn't work at all.Answer: No answer needed.
[Question 4.5] After the scan completes, which ‘Vulnerability’ in the ‘Port scanners’ family can we view the details of to see the open ports on this host?
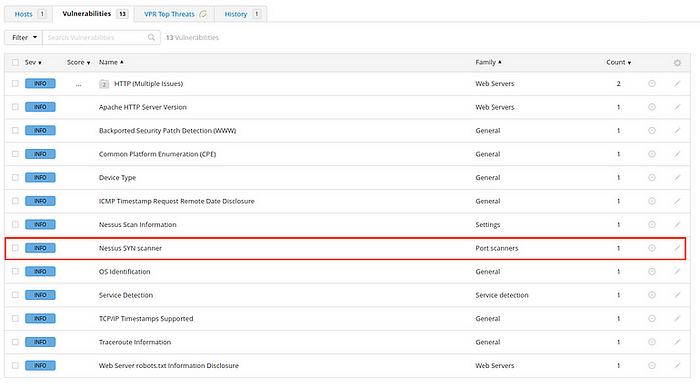

Answer: Nessus SYN scanner
[Question 4.6] What Apache HTTP Server Version is reported by Nessus?

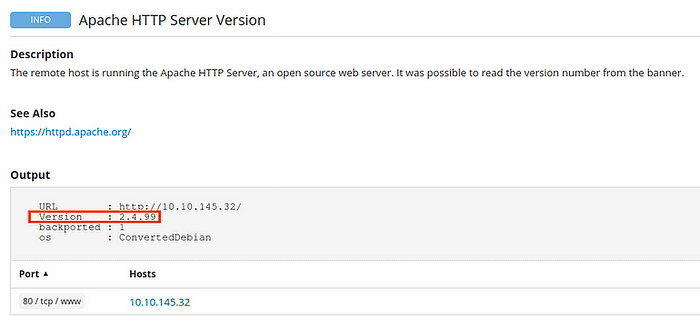
Answer: 2.4.99

Please be patient as this scan takes some time to complete.
[Question 5.1] What is the plugin id of the plugin that determines the HTTP server type and version?

You can locate it by looking for “HTTP (Multiple Issues)” and then “HTTP Server Type and Version.”
Answer: 10107
[Question 5.2] What authentication page is discovered by the scanner that transmits credentials in cleartext?

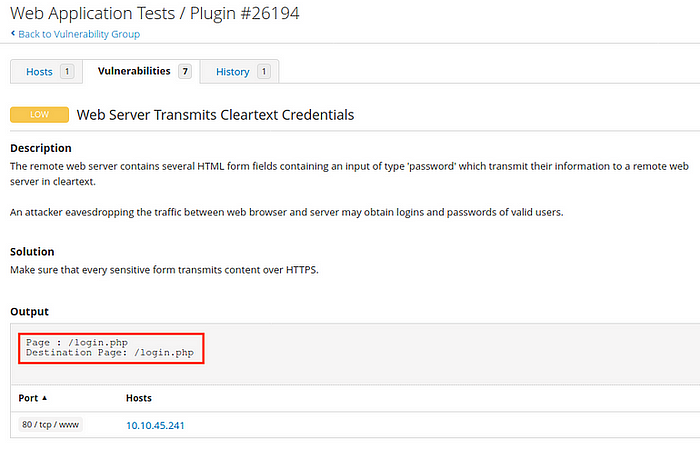
Answer: login.php
[Question 5.3] What is the file extension of the config backup?


Answer: .bak
[Question 5.4] Which directory contains example documents? (This will be in a php directory)
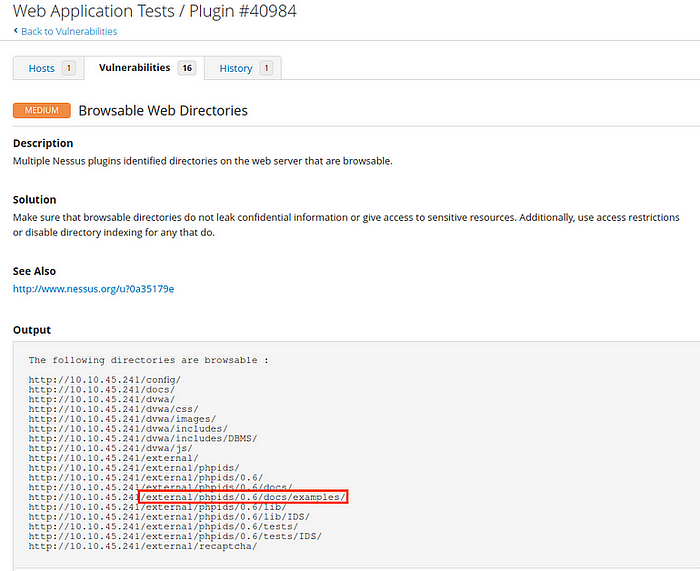
Answer: /external/phpids/0.6/docs/examples/
[Question 5.5] What vulnerability is this application susceptible to that is associated with X-Frame-Options?

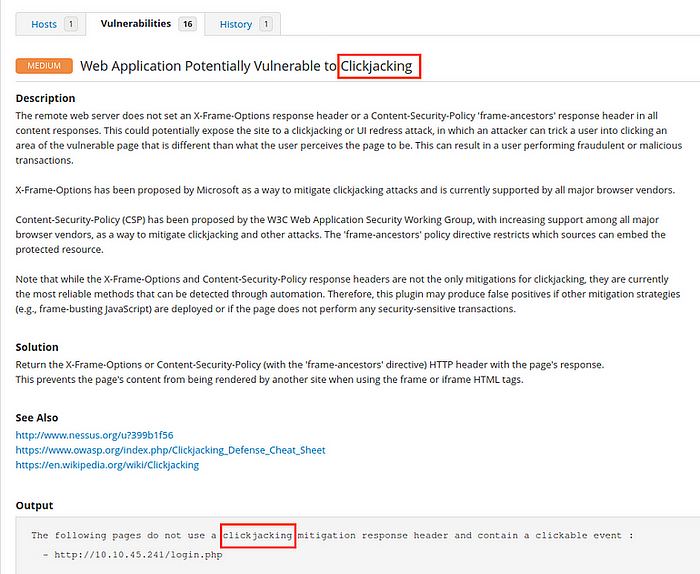
Answer: clickjacking
